[vulnhub] LampSec-CTF7
Last Update:
Word Count:
Read Time:

靶机部署
这台机子将其网卡设置为eth0。实际上的网卡是eth1。因此,我们需要删除配置文件/etc/sysconfig/network-scripts/ifcfg-eth0,并创建一个名为ifcfg-eth1的新文件。必须写在文件中的设置是ONBOOT=yes BOOTPROTO=dhcp DEVICE=eth1 #要配置的网卡名。然后service network restart就可以了。(在Cent OS 6中, 在大于等于7的版本应该使用systemctl)
其实之后最好把靶机丢到vm里面选择已经移动别选复制,这样容易保障网络环境配置不出问题。
信息收集
1 | |
1 | |
还开了挺多端口的,80,8080,139,10000都可以看看。
1 | |
1 | |
趁其它还在扫描的时间先看看80端口吧。
EXPLOIT
web
先目录发现一下,扫描的同时自己手动看看网页。
1 | |
随便点点,发现有几个可以输入注册的地方,以及8080端口是个登录页面。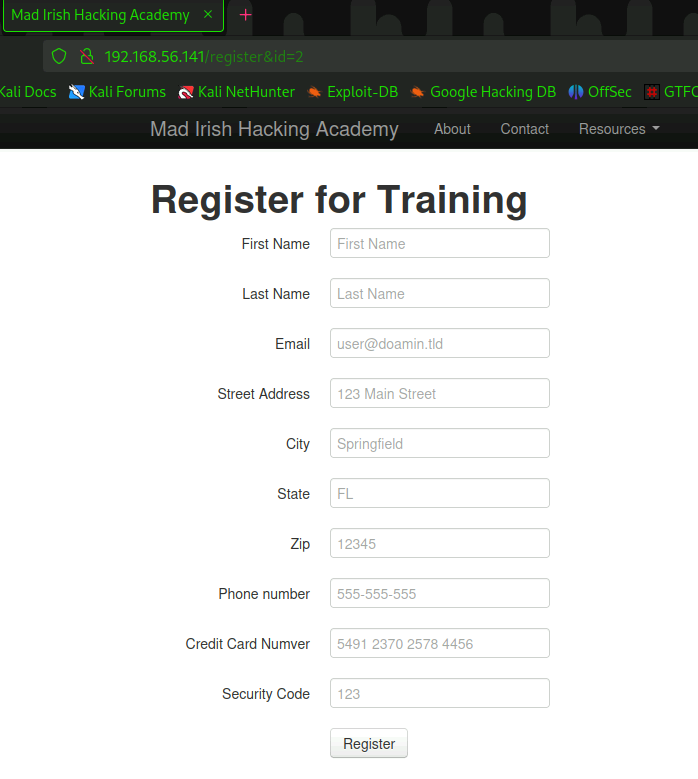
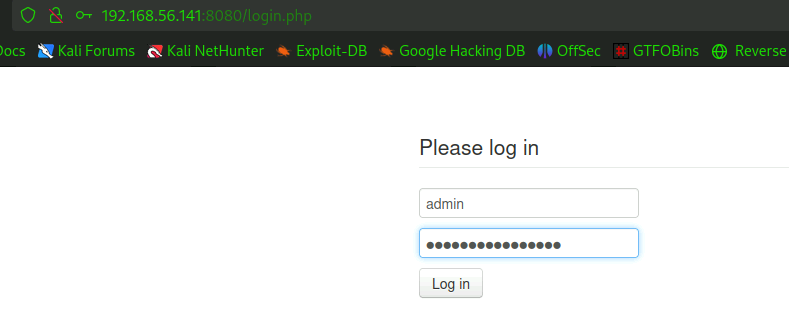
SQLi
加点'看看有何反应。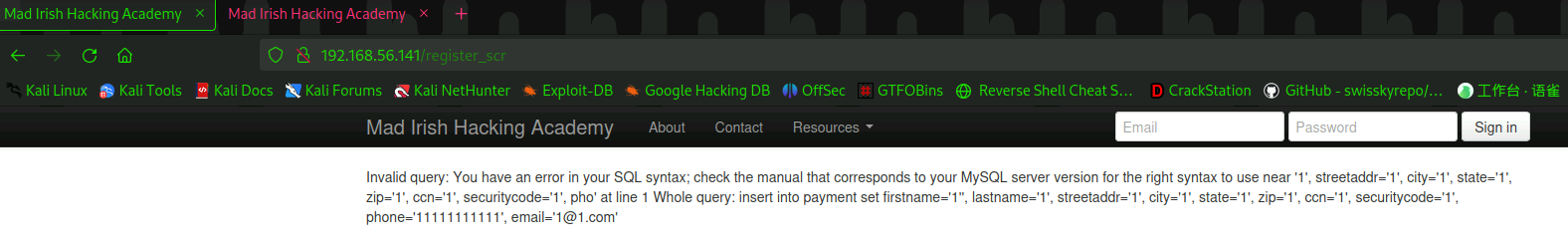
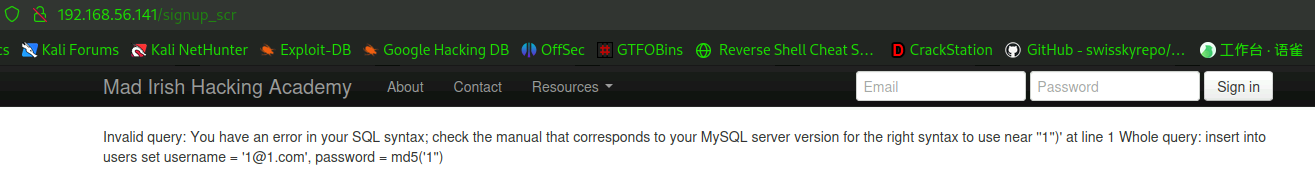
OK,存在sql注入漏洞。之后看看是否用sqlmap把库dump出来看看。
再在登录页面试试。
1 | |
竟然直接登进来了。
文件上传
ok,不过一时间看不出是什么cms,那就找找有无什么可以上传文件的地方呗。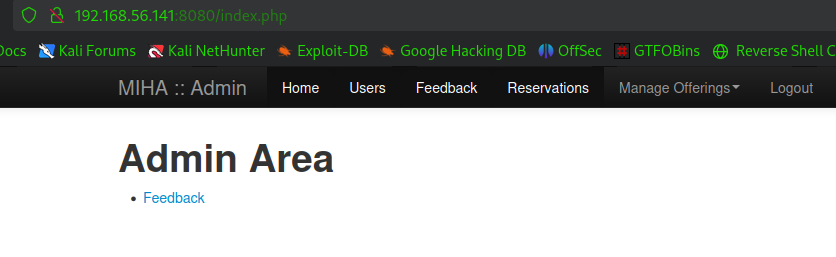
幸运的是我们找到了可以传文件的地方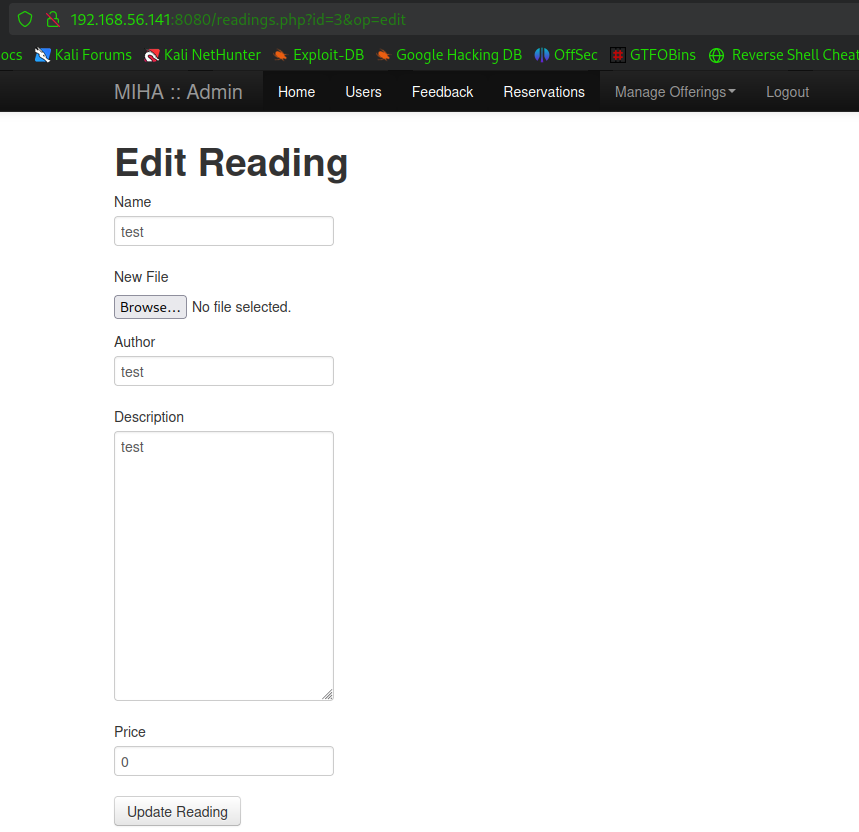
我们尝试利用文件上传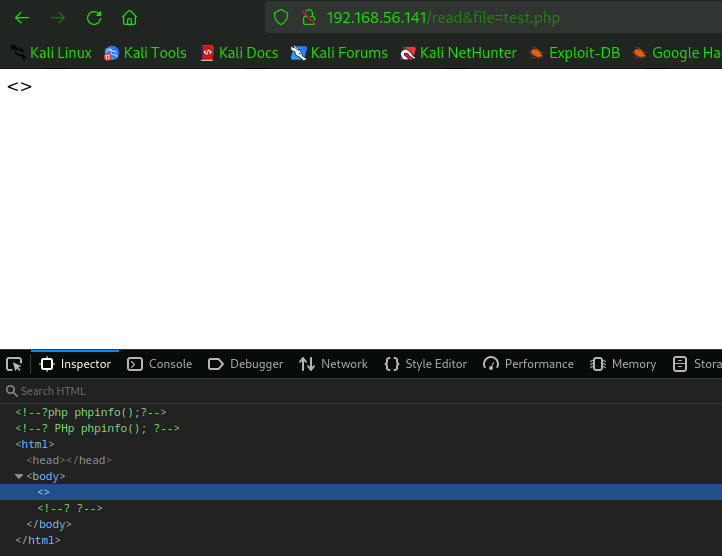
Seems that the <?and?> are filtered. However, even if we try to bypass the filter like <sript language="php">payload</script>, the payload just doesn’t work.
As a result, we must find the path of the uploaded shell.
Oh, don’t forget we did web content discovery and it was done for sure. So let us take a look at it.
1 | |
After some munal try, we find out upload file in the path of 192.168.56.141/assets/.
So we upload php-reverse-shell.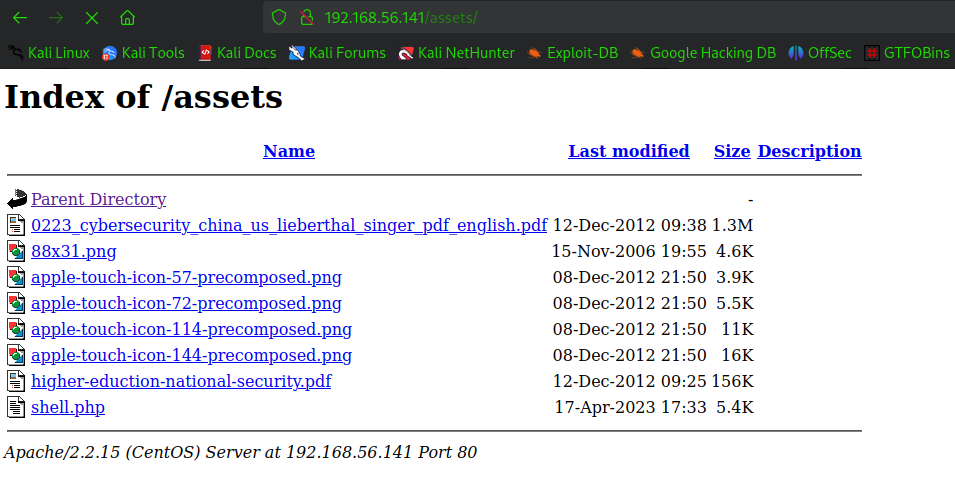 And we curl our
And we curl our shell.php
1 | |
Sucessfully get webshell.
Privilege Escalation
先python spwan一个更稳定的shell。
然后sudo -l需要密码,findsuid位文件没有能用的,cat /etc/crontab直接没有定时任务。OK。
行吧,在上大招前先手工枚举一下吧。
1 | |
版本挺低的,还是经典2.6,可以考虑内核提权。但是优先级往后稍稍吧。
配置文件查看
cd到/home目录下,发现很多用户,然而没有read权限,没用,查不了是否有用户遗留的登录凭证。
那就看看网站配置文件啥的吧,找点前后端连接用到的密码。
1 | |
从网站config文件我们可以看到,数据root用户登录直接不用密码。那我之后可以登录一下数据库找点信息。
敏感信息泄露
再手动遍历了下网页目录,发现之前进不去的/backups目录有个备份文件。我们查看一下,刚好最后几行记录了向数据库插入用户的账号密码等信息。
1 | |
我们提取一下登录凭证,把哈希值丢到crackstation。然后用得到的密码尝试直接ssh看看能不能成功登录。
1 | |
试到第3个john的时候就成功了。
1 | |
直接是sudo用户组的,直接提权成功。
密码复用
当然,我们也可以登录mysql数据库查看用户与密码。
1 | |
将这些凭证用sed与awk处理后,将hash值直接丢到hashcat中破解。
1 | |
我们用这些凭证进行密码喷洒攻击。
1 | |
非常OK。