[HTB] PC
最后更新时间:
文章总字数:
预计阅读时间:
页面浏览: 加载中...

前言
懒得写了,干就完了。
信息收集
nmap
1 | |
就发现开了22和50051端口,并且50051端口是啥也没扫出来。没有获得啥太好信息。
服务探测
不管50051端口是啥,我们先浏览器访问一下,结果返回一堆乱码,解码一下好像也是无意义字符。看不出来50051端口到底跑的啥服务。
看看chatgpt怎么说:
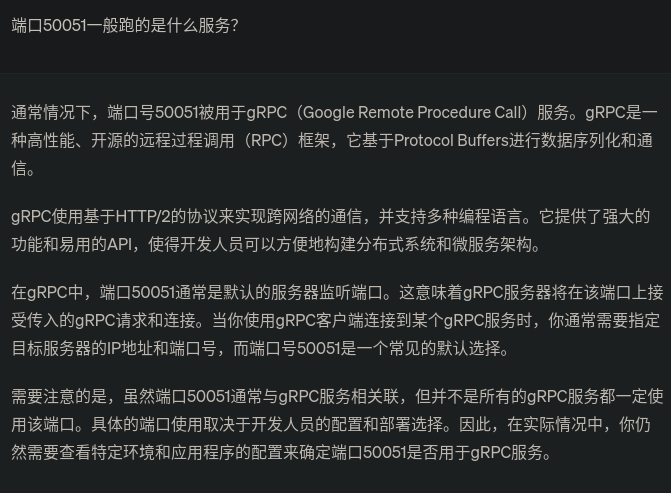
为了防止chatgpt胡说,我们再google一下,发现确实50051是gRPC的默认端口,那么这台机子很有可能就跑的是gRPC服务。
那我们再google一下gRPC exploit,发现了一篇很详细的介绍了gRPC安全问题的文章。文章中介绍gRPC SQL注入那段很详细的描述了gRPC的利用过程。
虽然我们并不知道这台机子上的gRPC是否存在SQL注入漏洞,但是前面的连接gRPC的步骤是通用的,我们照葫芦画瓢收集下信息再说。当然当务之急是先把grpcurl和grpcui安装好,这个在github上下载对应版本的release即可,有go环境的可以直接用git安装。
gRPC信息收集
1 | |
简单的用grpcurl探测一下,发现50051端口上跑着的gRPC服务叫SimpleApp且有三个服务。那我们下一步就是用grpcui与它交互。
1 | |
然后我们访问本地网址就能看到页面。
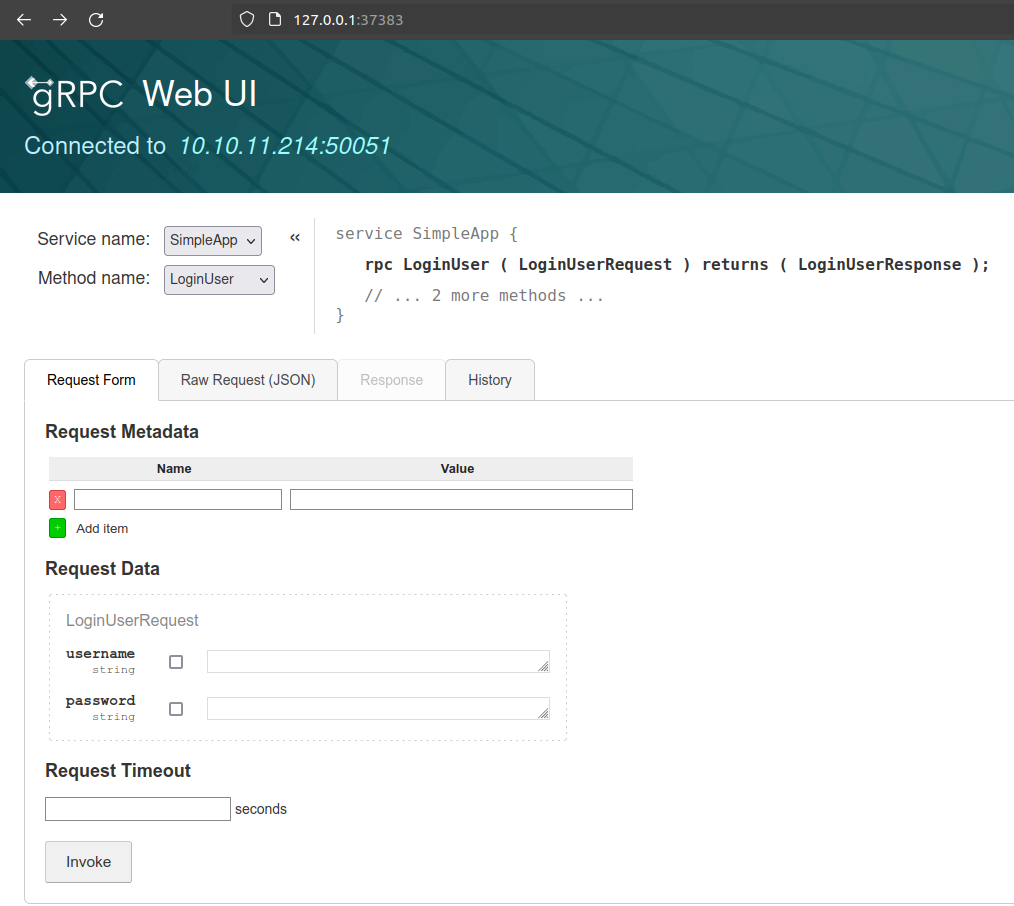
如果我们尝试注册账户,然后利用注册的账号登录,就会返回一个id以及token。
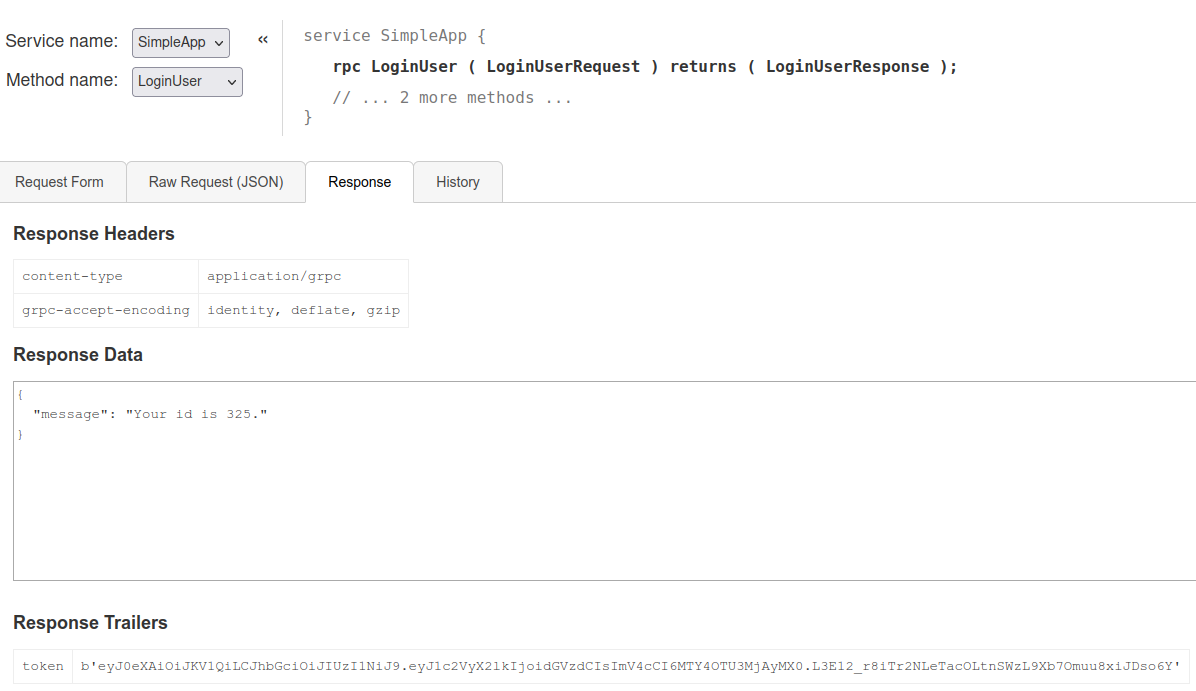
然后我们去用这个id和token去请求getInfo服务,就会返回:
1 | |
它给这id是啥意思,我们再创一个账号发现id是随机的,并不是规律递增,但如果我们请求id=1会返回一条不一样的信息:
1 | |
这难道暗示id=1的账户是admin吗?那我们尝试一下用admin登录一下,弱密码admin:admin一下就成功了。然而好像也没啥用,试了试好像用谁的token都可以任意访问id。
但换句话说好像也有用,这id的请求感觉没做任何限制很有可能存在脆弱性。加上我们之前看的那篇文章不就是利用gRPC上的SQL注入漏洞嘛,那我们就试试看究竟会不会有这个漏洞。
我们直接把请求保存成一个request.txt文件(用burpsuite或者火狐直接把请求复制出来都可以)准备用SQLmap看看是否存在漏洞,而且既然有admin权限的我们就用admin权限的,聊胜于无。
漏洞利用
SQLmap
sqlmap小测一下。
1 | |
发现后端数据库用的是SQLite且确实存在SQL注入漏洞,在指定--tables以及--columns查看了下大致的表与列真是换,发现数据量不大之后,我们偷懒直接把数据库dump出来(真实情况下请勿dump!dump几十条数据下半辈子就要无忧了)。
1 | |
我们拿到了一个sau用户的登录凭证,那自然是要去ssh试试的。
获取立足点
1 | |
发现成功登录,在home目录下拿到了user flag。
提权
上来就发现里面文件乱糟糟的,啥都有,先给机器reset一下再说。
三连
reset完就很清爽。依然是熟悉的sudo -l、find SUID bins以及cat crontab三步走。也依然是熟悉的啥也没发现。
漏洞发现
不管三七二十一先把linpeas以及pspy传上去再说。在我们将其传到/tmp目录下,正准备linpeas看一眼的时候,我们发现tmp目录下有个pyLoad目录,不仅如此,它还是root所有的权限为755的目录,这不是邀请我们进去看看吗,却之不恭,看看再说。
1 | |
发现里面有flask和jinja,明显是python模块,此外还专门放了个pyload.pid文件告诉我们pyload运行的pid是105。这pyload是几号人物,给这么多画面。
好奇宝宝直接进行一个谷歌的查pyload exploit是不是有猫腻。结果我们确实发现了其存在Pre-auth RCE in pyLoad的漏洞。且github上有详细的PoC。
漏洞定位
那么现在是道理我都懂环节了,但是这个pyload究竟跑在哪里,跑在什么端口呢?
我们直接netstat -nat看一看。
1 | |
做个排除法,跑在本地显然不是22,那就是8000或者9666了。
我们先curl看看8000端口什么情况。
1 | |
看来是跳转了,我们用ssh端口转发到本地,用浏览器打开看看。
1 | |
访问一下网站:

发现确实是pyload服务,那我们就完成了pyload服务的定位。
PoC验证
我们试试8000端口能否验证PoC。
1 | |
一发入魂,虽然返回报了500,但是文件确实以root身份创建了。也就是说我们能以root身份进行任意命令执行。那就简单了,给bash赋s位,写入sudoer都行,但是考虑到是多人共用靶机,我们选用影响最小的方式
提权到root
影响最小的方式当然是反弹shell了,我直接创建一个名叫exp.sh的shell脚本反弹shell。
1 | |
本地nc监听成功拿到root shell。
1 | |
成功拿到root flag。